One Dashboard. Every Detail.
Petadot’s Web Vulnerability Scanner makes securing your web assets simple, fast, and reliable. Our interactive dashboard gives you a complete view of your risk posture from detection to remediation.
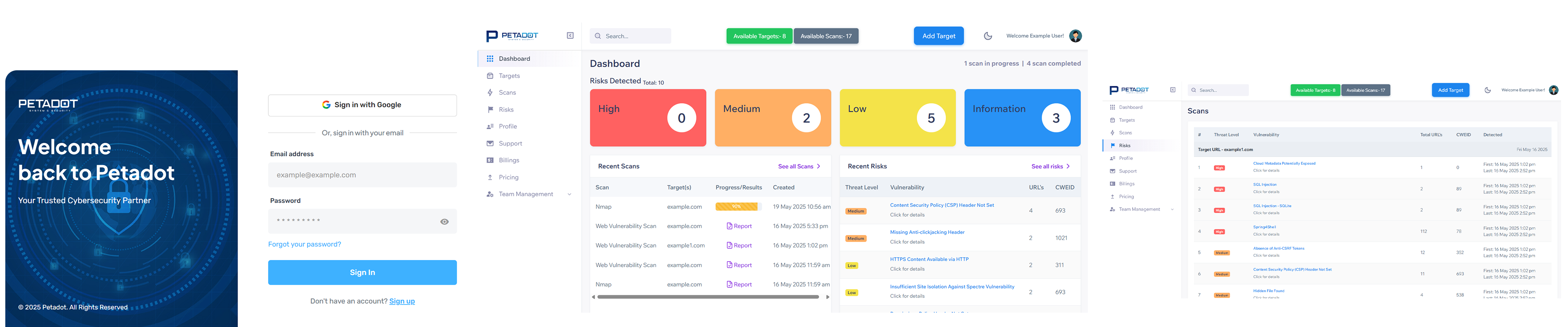
Petadot’s Web Vulnerability Scanner makes securing your web assets simple, fast, and reliable. Our interactive dashboard gives you a complete view of your risk posture from detection to remediation.

Each scan generates a detailed PDF report highlighting vulnerabilities, severity levels, affected URLs, and recommended fixes

Identify known vulnerabilities, misconfigurations, outdated components, and exposed services across all layers.
Automates detection, reduces manual effort, and accelerates the vulnerability management lifecycle.
Detects vulnerabilities based on recognized standards (OWASP Top 10, CVE)
Reports are designed with clarity — making them easy to understand for both tech and non-tech Persons.
Every scan includes powerful features designed for developers, startups, and enterprise teams:
Detects common and advanced web threats like: SQL Injection, XSS, Insecure Auth & Sessions.
Leverages AI and advanced heuristics to simulate real-world attacks.
Get in-depth insights with severity ratings and remediation recommendations.
Prioritize threats by impact. Focus on what truly matters for your business.
Run vulnerability scans at Your Fingertips
Identify and eliminate vulnerabilities
Real-time monitoring & alerting
Proactive threat hunting
Rapid investigation and recovery

Scan And Protect Your Entire Digital Footprint With Our Comprehensive Scanning Capabilities
Advanced scanning for web app vulnerabilities including OWASP Top 10 like XSS, SQL Injection, CSRF, and misconfigurations.
Comprehensive assessment of servers, devices, and open ports to detect vulnerabilities and secure your network layer.
Perform online scans of backend servers and APIs to detect vulnerabilities and misconfigurations, enhancing the security of your web applications.
Leverage the most trusted security tools in the industry, enhanced with our proprietary technology
Scans your website to find and report security issues or weaknesses.
Finds devices and services on your network to spot potential risks.
Checks your encryption settings to make sure data stays private and secure.
Uses AI to analyse and find out the vulnerabilities in your Infrastructure.

Simulating an external attack with no prior system knowledge, Blackbox testing identifies vulnerabilities exposed to outside threats—offering a real-world view of your system’s public-facing weaknesses.
With full access to internal systems, Whitebox testing delivers in-depth insights into infrastructure, applications, and security controls—ideal for uncovering complex internal vulnerabilities.
Combining external and internal perspectives, Greybox testing leverages limited access to simulate targeted attacks—balancing realism with informed analysis.
It is recommended to run scans:
After scanning the report will be a thorough PDF that includes: